This article delves into hackers’ forums, shedding light on their dynamics, motivations, and the broader implications for cybersecurity. These hackers’ forums, also known as underground communities, offer a unique glimpse into the world of cybersecurity from a different perspective. In the vast expanse of the internet, hidden beneath the surface, exist online forums where hackers and cybercriminals convene to share knowledge, tools, and insights. By leveraging the capabilities of this tool, businesses can fortify their payment processing systems, prevent fraud, streamline operations, and foster trust with customers.
Conclusion: The adoption of BIN Checker Software underscores business owners’ commitment to security, compliance, and customer experience. As the digital landscape continues to evolve, BIN Checker Software remains a valuable asset in the arsenal of modern businesses seeking to navigate the complexities of online transactions while ensuring integrity and reliability. Phishing and Identity Theft: In one well-known case, fraudsters sent convincing phishing emails purportedly from a legitimate financial institution.
The emails requested recipients to update their account information urgently. Unsuspecting victims clicked on the provided link and unknowingly shared their dump credit card numbers card details, leading to unauthorized transactions and identity theft. Cybercriminals seek to monetize the stolen data by making fraudulent purchases, withdrawals, or other illicit financial transactions. Financial Gain: The primary motive behind hacking card dumps is financial gain. Conclusion: The allure of using stolen personal information from live fullz can be tempting, but it’s essential to recognize the legal and ethical implications.
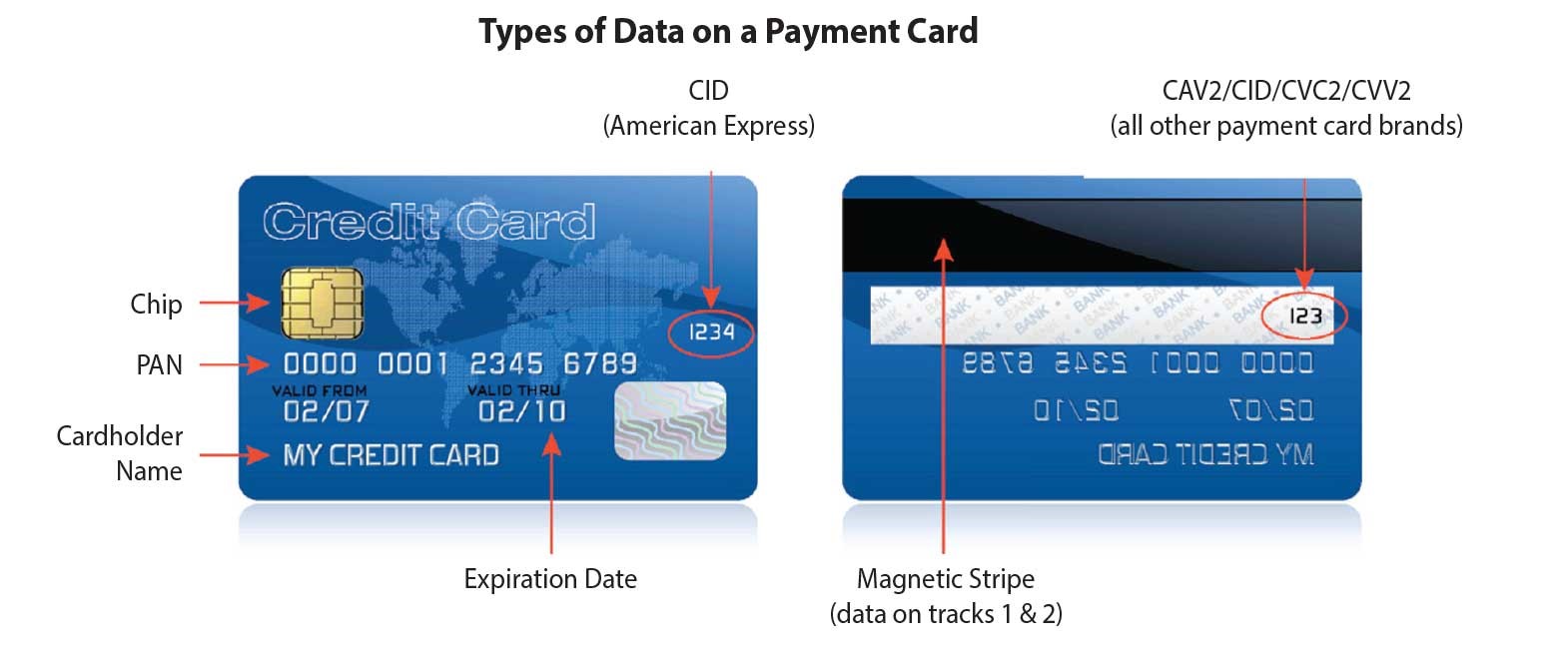 Engaging in the purchase and use of live fullz supports criminal activities, undermines personal privacy, and jeopardizes the financial security of innocent individuals. By avoiding these illegal activities, individuals can contribute to a safer digital landscape and uphold the values of legality, ethics, and respect for privacy. A complete set of personal information allows criminals to impersonate individuals, make unauthorized transactions, and even commit tax fraud. Understanding Fullz: Fullz are prized possessions in the underground world of cybercrime, as they provide cybercriminals with the tools to commit identity theft, financial fraud, and other illicit activities.
Engaging in the purchase and use of live fullz supports criminal activities, undermines personal privacy, and jeopardizes the financial security of innocent individuals. By avoiding these illegal activities, individuals can contribute to a safer digital landscape and uphold the values of legality, ethics, and respect for privacy. A complete set of personal information allows criminals to impersonate individuals, make unauthorized transactions, and even commit tax fraud. Understanding Fullz: Fullz are prized possessions in the underground world of cybercrime, as they provide cybercriminals with the tools to commit identity theft, financial fraud, and other illicit activities.
